Web Pentesters Can't Do CTFs? Hold My Shell.
What’s good everyone!
So, something a little different happened recently. I decided to dive head-first into the Cybercon CTF challenge for KNUST. Now, most of you know me as a web application penetration tester. My day-to-day is hunting for XSS, SQLi, and messing with business logic. I barely touch CTFs, but I figured, why not?
Long story short, I walked out with 2nd place and some Cybercon swag. 
It got me thinking. The core skill set we use in penetration testing,that deep-seated need for problem identification is 100% applicable to CTFs. You’re still identifying weaknesses and figuring out how to exploit them. The approach, though? The thought process is a whole different beast.
How RAWPA’s Methodology Bridged the Gap
This is where my own tool came in clutch. My thought process was seriously buttressed by RAWPA’s neural pathway methodology feature.
At one point, I was staring at an endpoint, trying to get initial access. The path forward wasn’t obvious. Instead of getting lost in endless Google searches or trying random scripts, I leaned on RAWPA. It gave me a set of clear approaches to gain the flag. And let me be clear, this stuff is very technical you must know what you’re doing to understand the guidance. It’s not a magic button.
It paved the way to get initial access on one of the endpoints through SSH using a private signed key. lol.
The methodology laid out the quickest approach in about 4 steps (more like fallback alternatives). It was like having a master strategist whispering in my ear. “Try this first. If that fails, pivot to this. If that’s a dead end, here’s your third option.” It would’ve taken me a while of searching to figure that out on my own. 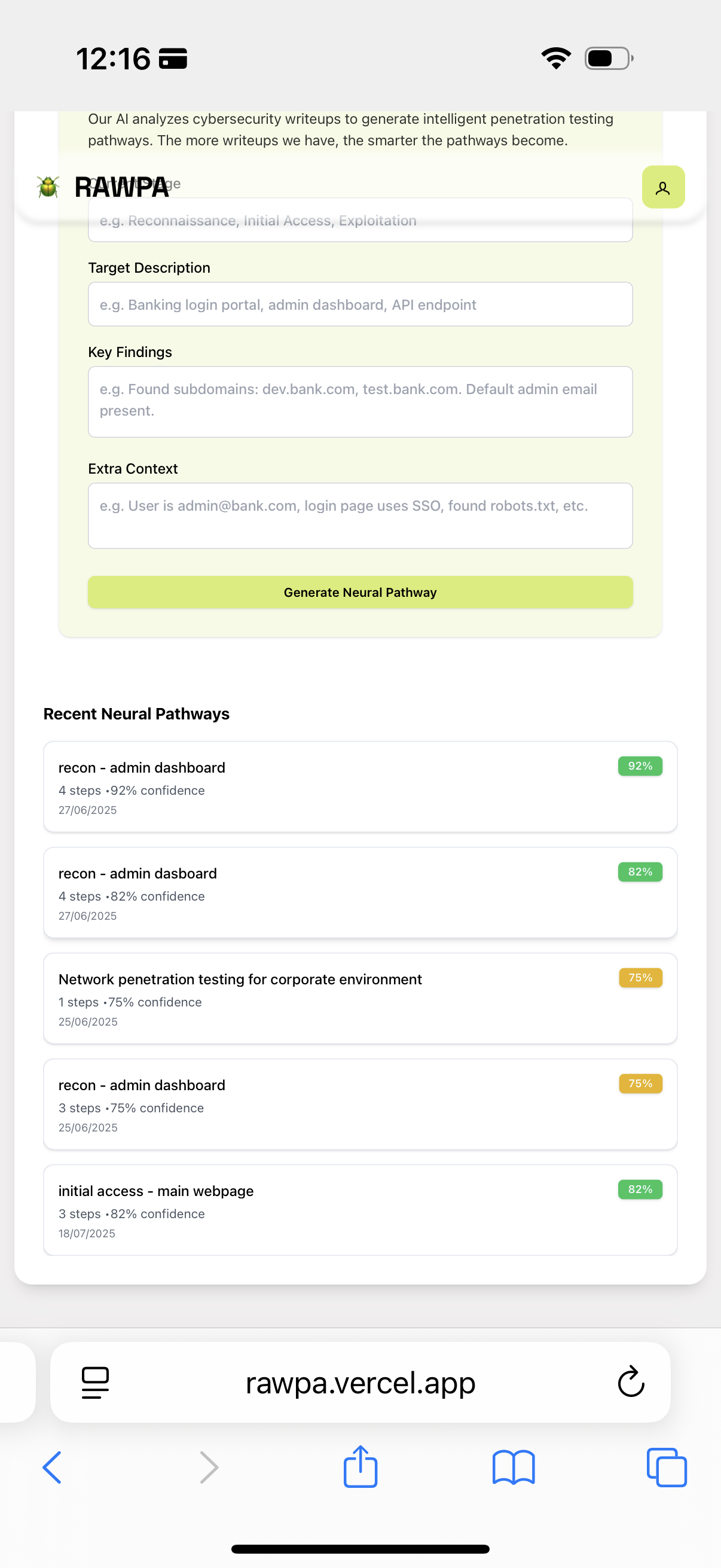
You may ask why this Methodology is named “Neural Pathway” because it learns from a knowledgebase. Refer to my previous posts to read about it or shoot me a message on Linkedin and I’ll write about it briefly on here.
The Road Ahead
Unfortunately, I came in 2nd. Next time, I’ll go harder. The experience proved to me that my strategic thought process, especially when augmented by RAWPA, is solid. But it also highlighted a weakness: the commands and the traditional CTF approaches. The muscle memory just wasn’t there.
So, I guess I have to finally finish those beginner boxes in Hack The Box and officially add CTF practice to my learning process, alongside my labs.
This article was short, but the lesson was huge.
Quick Update on RAWPA
Speaking of the lab, here are some quick updates on the project:
- Hunter’s Board: I’m adding the finishing touches. The collaboration feature has been added, so you can work together on assessments.
- Bug Fix: Squashed a nasty error that was spamming my Firebase server with a ton of POST requests. Things should be much smoother now.
- UI/UX: Added a collapse card button on all cards. This lets you get a more tidy and cleaner-looking board. I use Obsidian a lot, so I know where I want the Hunter’s Board to go aesthetically and functionally. It’ll just take time to build it out.
The Hunter’s Board also really came in clutch to keep my thought train moving straight. With the new collaboration feature, teams can even use the dashboard during CTFs or penetration testing as a team. 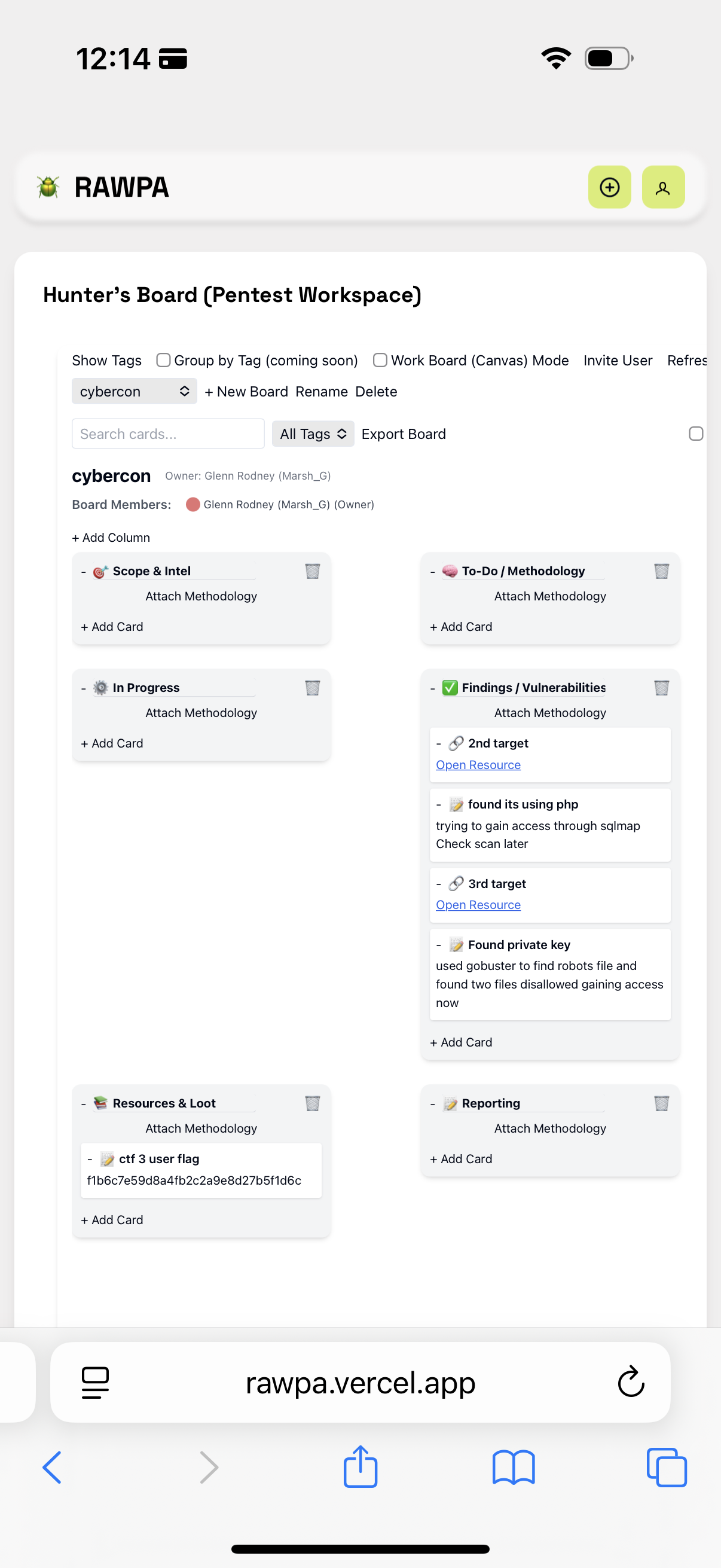
kuwguap out. catch yall inna bit. cheers.